








Businesses, individuals, and other entities rely on the online market to perform any course of action. This heavy technological reliance on storing and transmitting personal and confidential data increases the percentage of data breaches and website security concerns. People are improving and adapting new security policies and methods to safeguard their sensitive data. As a web development agency, we will talk about 5-important points on how to secure your website from web threats.
Always run the code on your server. If your website depends on your server only and not any other server, you become the complete owner. This way, you are not letting anyone else handle your site security. Amongst several website security measures, here are 5-essential factors you may need to consider:
Websites that deal with sensitive data collection and transfer, such as login credentials, banking information, contact details, and more, need Hypertext Transfer Protocol Secure (HTTPS). For example, (https://xyz.com), this is what an SSL-certified website domain looks like. It follows a security protocol- TSL (Transport Layer Security), an updated version of SSL (Secure Sockets Layer). Using TLS/SSL helps clients (web browsers) protect data through encryption and verify the server’s authority and integrity while connecting to the web. Sites with SSL certificates utilize DoH (DNS over HTTPS) protocol to encrypt DNS queries to eliminate DDoS attacks. It keeps your data private and sets limitations for network administrators or web visitors to capture your online behaviours.
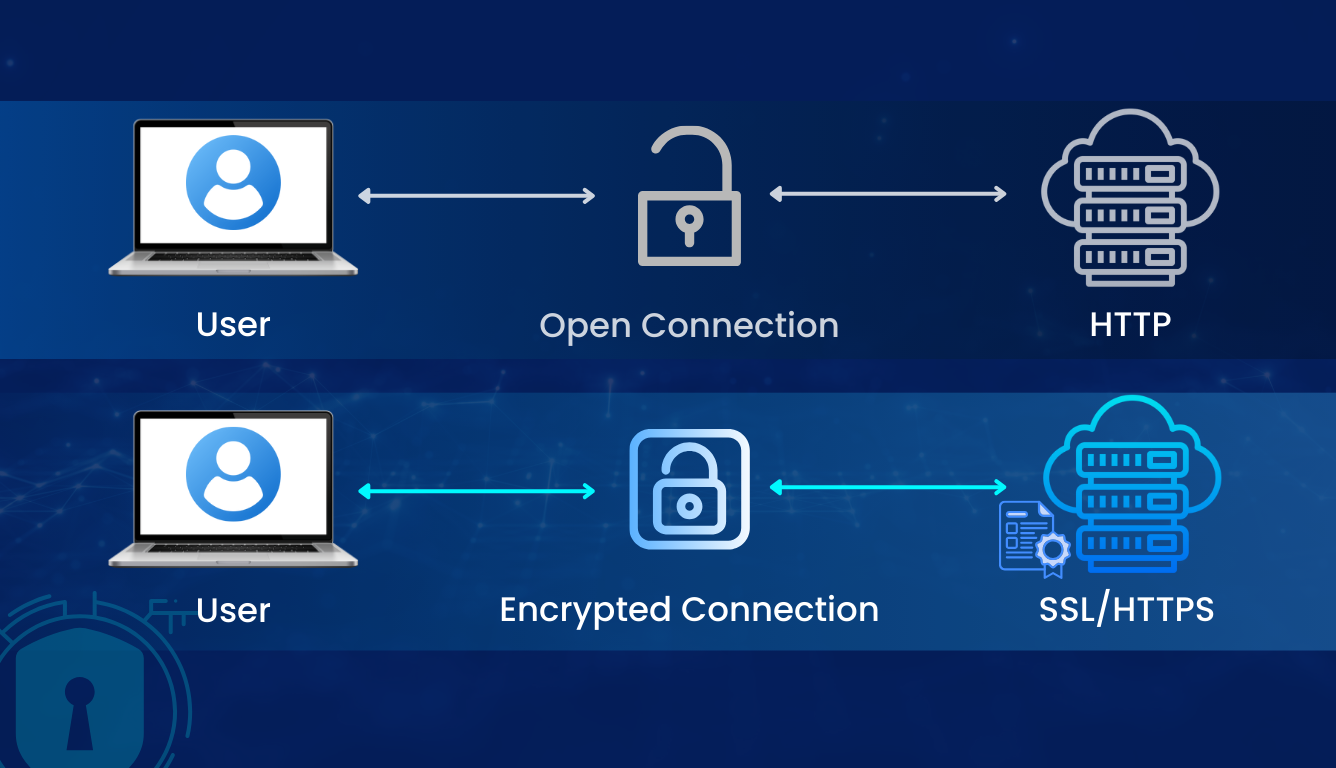

Additionally, implementing SSL/TLS lowers page loading latency, and websites with HTTPS URLs get better search rankings on Google and other search engines. Generally, you can get a free SSL certificate from your hosting provider or purchase it at an affordable cost. Take note that an SSL certificate comes with an expiry time, and missing updates or renewals might harm your website’s security.
A web application firewall is another integral component of website security that uses a specific protocol to examine suspicious activities and unverified incoming HTTP traffic coming to your site. It helps you protect your site in real-time against web attacks, such as cross-site scripting, DDoS, SQL injections, and other malicious actions. Host, Network, and Cloud-based approaches are the available categories of WAF.
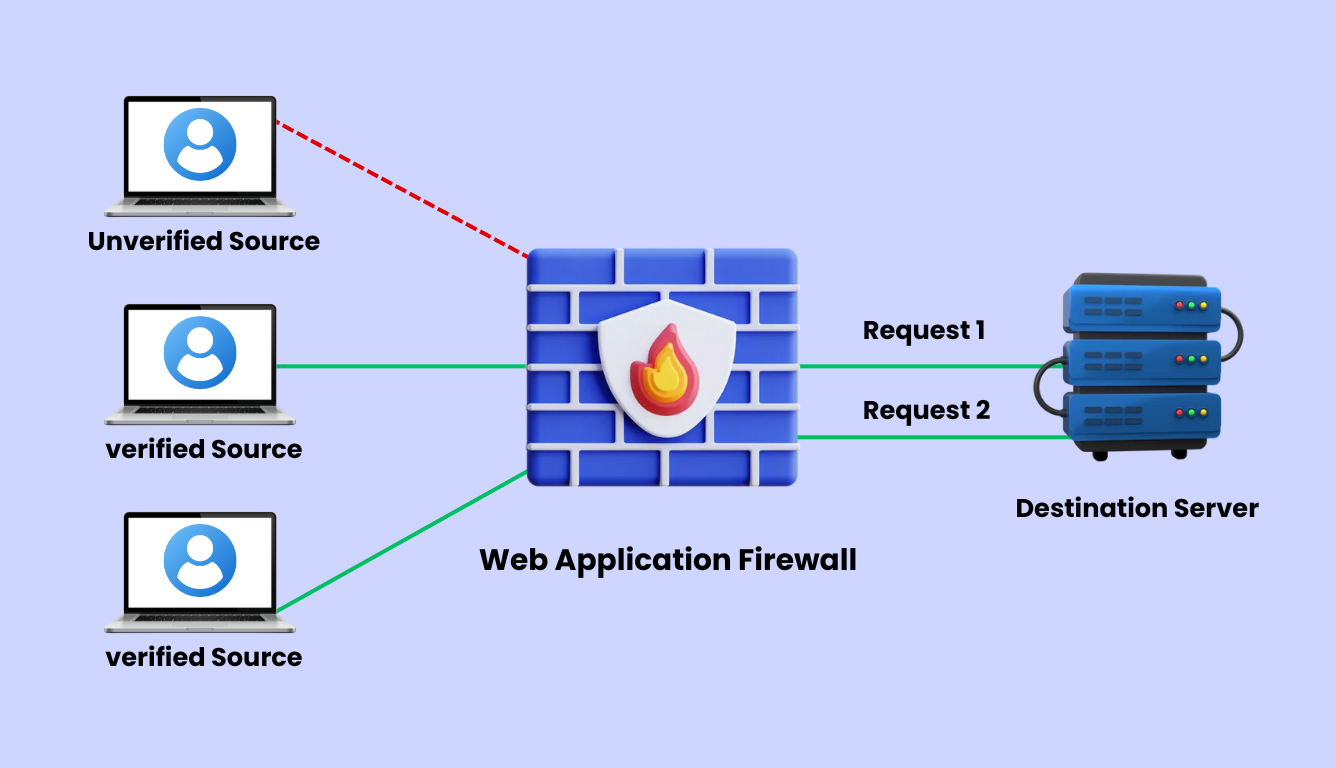

Even though a WAF and standard firewall system provide web security, they perform on different OSI (Open System Interconnection) layers. For instance, a firewall creates a barrier to separate external and internal web traffic through DNS traffic/packet filtering, Proxy algorithms, and other protocols. On the other hand, a web application firewall scrutinizes the HTTP communication between web applications and web users. WAF is a part of a firewall system with a few advancements in security functionalities.
Updating plugins and system applications makes your site operational and secure. Specifically, WordPress-based websites use several free and premium plugins to enhance the site’s performance. Always remember using a plugin from any unverified source might make your site vulnerable, and hackers can easily inject malware and malicious codes to control your site.
As a plugin development and integration company, we suggest you never avoid plugin updates for security patches that address potential web threats and other website functional drawbacks. Consider these factors for plugin updates:
Another fruitful way of saving data against web attacks is regular site backup. If you keep data copies and store them separately in a specific secure location, you can easily organize and recover files during site crashes or unusual incidents. Additionally, practising data backups helps you structurize non-synchronized and old data. You get accessibility to revive data to a certain point in time and minimize data loss.


So, how do you take regular data backups? Several processes you can adopt for data recovery and backups. The most convenient ways are:
Setting up access control and permissions to the site’s data files reduces the risks of cyber threats and data breaches. The intention of implementing access control is to streamline the access management permissions of several users. You can add definite roles to the site’s users and admins to perform respective operations. It will help you to check the running activities of your site and undo any unauthorized changes or deletions of data that happen on your site.


You can apply access control in several methods, such as MFA (Multi-Factor Authentication), user role-based access privileges, strong password protection, login attempts, and automatic logout sessions. It is important to update user permissions to restrict file uploads to specific users after validating the uploaded files to execute the intervention of malicious scripts. For example, Files: 644 or 640
Directories: 755 or 750
Restrict access to sensitive files like .htaccess, wp-config.php, or configuration files.
Cybersecurity has become a significant factor in protecting web data. The necessity of data protection is evident with the increase of technologies. Website security is completely in your hands. If you do not allow it, no one can hack your site. So it is absolutely necessary to be careful. It is recommended to use strong passwords, restrict generic admin URLs for a website (example: abc.com/wp-admin), and change passwords at least once every 6-8 weeks can be crucial. Always change site credentials after a development team delivers the site to you. To get an in-depth idea about website security and data protection, you can contact us.
Website Development | Mobile App Development | Application Development
We will definitely get back in touch with you over mail within 12 Hours.
In-case you have not heard from us within 12 hours, kindly check your spam once.
I'm a software consultant. I've 7+ years of industry experience. I'd love to connect with you and brainstorm your custom software needs. It's my responsibility to find you the best solution.
ANAND GUPTA
Drop your details and we'll get in touch with you within 12 hours.
Reach us for
Talk to us